Azure Active Directory
Synchronise users and groups from your Azure Active Directory (Azure AD). Azure AD is an identity management service provided by Microsoft used by Office 365.
It is cloud only, and stores user and group information. These can come from Office 365 or synchronised from a traditional domain. It is not an LDAP compatible directory store and uses a different API. It has reduced functionality so It cannot authenticate users. Authentication must come from another source like ADFS orWindows Integrated Authentication.
Prerequisites
Before setting up your Azure Active Directory security sync within Workplace AI, you must first set up an Azure Registered Application and grant the required permissions.
Setting up you Azure Registered Application
Navigate to https://portal.azure.com.
Check you're in the correct Azure Directory.
In the search bar, type “App Registrations” or select "App Registrations" under Azure Services.
Select "New registration"
Name - Give the application a user friendly name.
Supported account types - Choose if the application will only be used in this directory. Or if it will be used in others too.
Redirect URI (optional) – This is not required.

Select "Register"
This gives you an overview of your application on the registered application page. You'll need the Application (client) ID and Directory (tenant) ID from this page later in the process.
Creating your application secret
In Azure Portal, select "Certificates & Secrets".
Ensure you are on the Client Secrets tab.
Select "New Client Secret".
Description – Add a description to the secret of what it will be used for.
Expires – Give the secret an appropriate expiry date.
Select Add.
Be sure to save your secret to a secure vault such as LastPass as you will not be able to view it again. This secret is now associated with the registered application in Azure.
Configuring your API permissions
Now you have a registered application with a secret, you can add API Permissions.
In Azure Portal, navigate to your registered application.
Under Manage, select API Permissions.
There will always be Microsoft Graph, User.Read permissions. This is required and should remain in place.
Select Add a permission.
Under Microsoft APIs, select Graph API.
Select Application permissions.
This ensures user credentials aren't required for authentication and the context is not scoped to one user.
From the available permissions, select
Directory.Real.All
Group.Read.All
User.Read.All
Member.Read.Hidden
Select Add permissions.
The permissions have been applied but not yet granted to the registered application. You must grant admin consent for any permission applied. This allows silent authentication for APIs. Without this the application needs a user invoked authentication flow.
Select Grant admin consent for .
Select Yes to confirm this selection.
The permissions have now been applied to the registered application for the Graph API.
Setting up your Azure AD Security Sync
Within the security configuration modal in Control Hub
Security System: Select Active Directory from the dropdown.
General
Authority URL: Enter the URI for your directory.
Often this is https://login.microsoftonline.com/ followed by the tenant name. This may not be the case for some types of Office 365 e.g. Educational or Governmental.
Credential: Choose the relevant credential for this token from the dropdown.
Scopes: Enter the scopes requested to access a protected API. Example scope form, ResoucreUri/.default.
Featured Domain Name: Enter the old style NETBIOS domain name.
This will be used when qualifying synced objects from an on-premise domain.
Managed Domain Name: Enter the Azure Domain Name.
This will get qualifying objects created from Azure Active Directory.
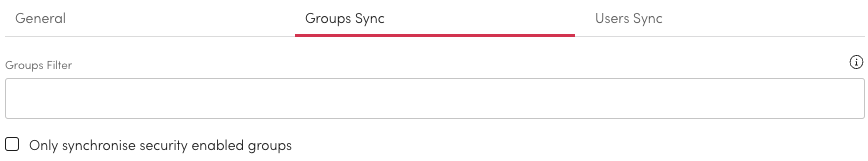
Groups Sync
This filter will be used when synchronising groups. Use the filter parameter syntax to retrieve a subset of a collection based on its properties. Support for creating a Parameter Syntax and How to determine group sync properties.
Only synchronise security enable groups is a predefined filter equal to (securityEnabled eq true). Enable this to synchronise only groups that can be used to secure access.
Users Sync
The user sync area should be used to filter in and out users from synchronising and also adding group.
Users Filters: Create filters used when synchronising users to Workplace AI. Create the filters using Parameter Syntax.
Synchronise Checkbox Setting: Control what users synchronise by checking either:
Synchronise federated (on-premise) users.
Synchronise managed (Azure AD) users.
All users will be synced, including some users that are neither federated or managed when neither are ticked.
Only Synchronise Licensed Users: Check this to filter out any expired accounts.
This is a predefined filter equivalent to (accountEnabled eq true).
Only Synchronise Enable Users: Check this to filter out users without an Office 365 license.
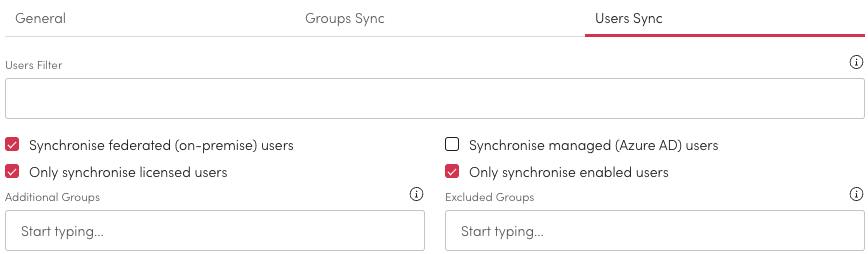
Additional Group: You can add a user group to Additional Groups. This must include the appropriate qualifier.
Excluded Groups: Enter any groups from users that you want to remove. This must include the appropriate qualifier.
Last updated